The increasing use of wireless networks has led to a rise in the number of cybersecurity threats, including Honeypot Access Point attacks. This type of attack can be very dangerous, as it can go unnoticed for a long time and can cause significant damage to your network.
In this blog, we will explore the concept of Honeypot Access Point attacks, how they work, and the impact they can have on your network.
What is a Honeypot Access Point Attack?
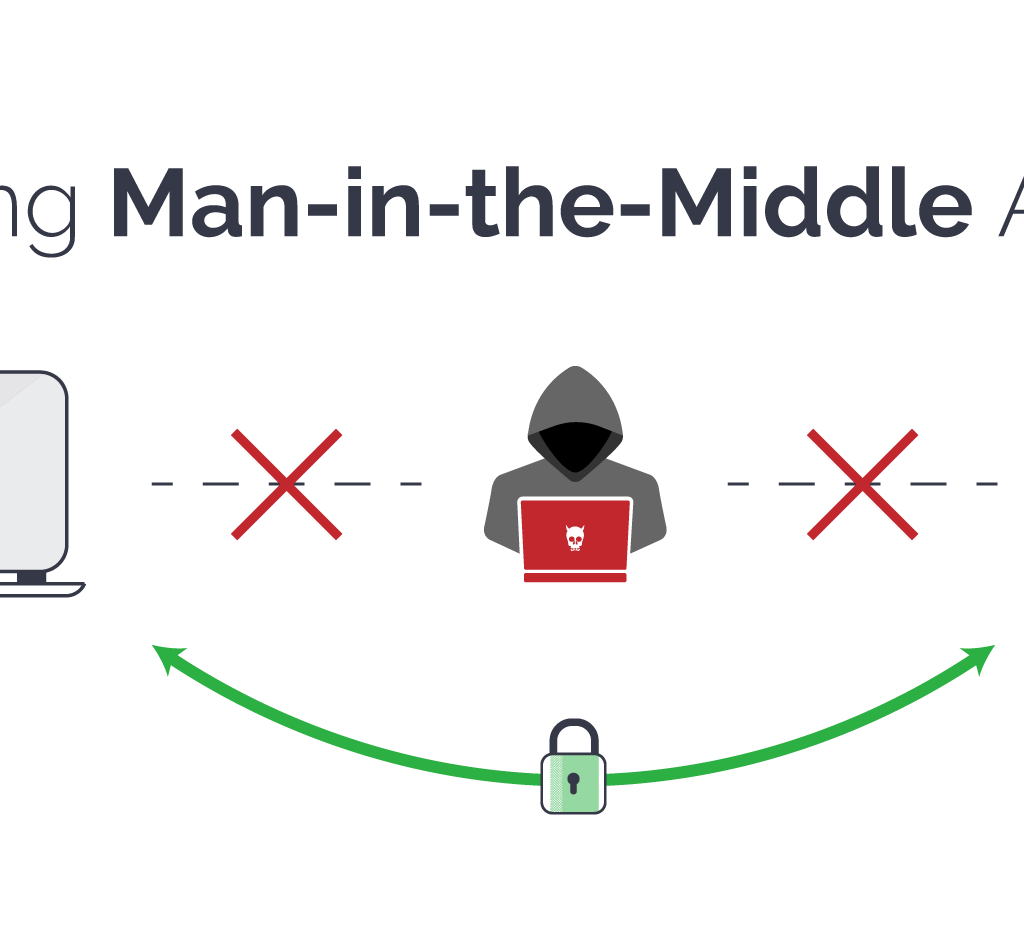
A Honeypot Access Point attack is a type of security breach that uses a fake wireless access point to lure unsuspecting users into connecting to it. The attacker then uses this connection to gain access to sensitive information and compromise the target’s network.
How do Honeypot Access Point Attacks work?
A Honeypot Access Point attack works by setting up a fake wireless access point that appears to be legitimate to users. The attacker then waits for a user to connect to the fake access point and then uses this connection to steal sensitive information or launch an attack on the target’s network.
The impact of Honeypot Access Point Attacks on your network
Honeypot Access Point attacks can have a significant impact on your network. Once the attacker gains access to your network, they can steal sensitive information, such as login credentials, financial information, and confidential business data. They can also install malware, ransomware, or spyware, which can cause further damage to your network.
Protecting your network from Honeypot Access Point Attacks
To protect your network from Honeypot Access Point attacks, you need to be vigilant and proactive. Here are some steps you can take to secure your network:
- Use strong passwords and change them frequently
- Install and regularly update anti-virus software
- Use a Virtual Private Network (VPN) to encrypt your internet connection
- Enable firewalls and intrusion detection systems
- Be careful when connecting to public Wi-Fi networks
Conclusion:
Stay Ahead of the Deception Honeypot Access Point attacks are a silent threat that can cause significant damage to your network if not detected and prevented in time. By being proactive and taking the necessary steps to secure your network, you can stay ahead of the deception and protect your business from this type of attack.