The use of web services has become increasingly popular, as they provide a convenient and efficient way for applications to communicate with each other. However, this convenience also makes them an attractive target for attackers. One particular attack that has gained attention in recent years is the Web Service Amplification Attack.
What is a Web Service Amplification Attack?
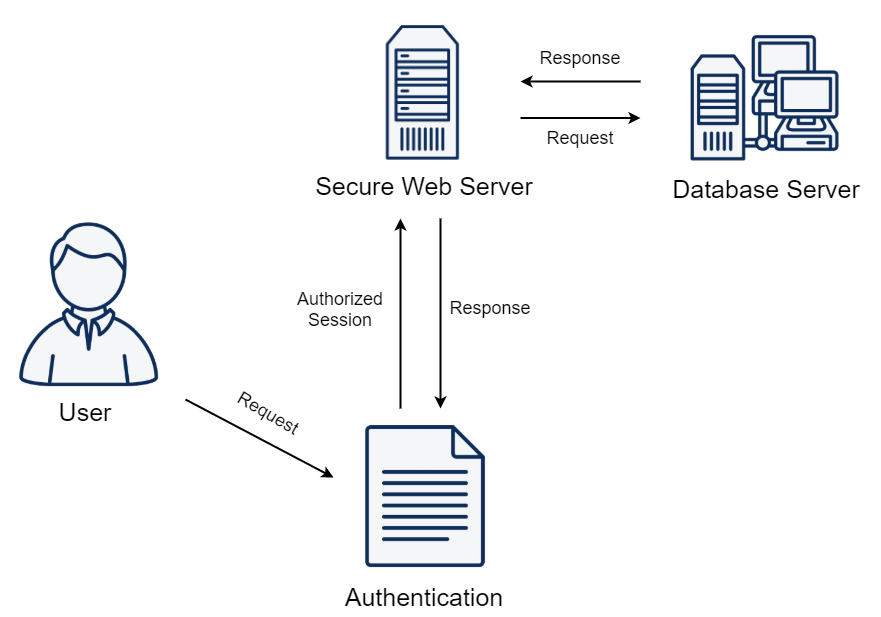
A Web Service Amplification Attack is a type of Distributed Denial of Service (DDoS) attack that targets web services by exploiting their design. It takes advantage of the fact that web services are designed to be scalable and efficient, by allowing multiple requests to be sent and processed at the same time. Attackers can send a small number of requests to a web service, but manipulate them to amplify the size of the response that is sent back to the target.
How Does a Web Service Amplification Attack Work?
Attackers use a technique called reflection to amplify their attack. They send a request to a vulnerable web service, but manipulate it to include the IP address of the target as the source address. When the web service responds, the response is sent to the target instead of the attacker, causing a flood of traffic to the target. This amplification technique can increase the size of the attack by a factor of hundreds or thousands, making it difficult to defend against.
Impact of a Web Service Amplification Attack
A Web Service Amplification Attack can have a significant impact on the availability of your network and services. The high volume of traffic generated by the attack can overwhelm your network infrastructure, leading to slow or unresponsive services. In addition, it can consume a large amount of bandwidth and resources, making it difficult for legitimate traffic to get through.
Preventing a Web Service Amplification Attack
Preventing a Web Service Amplification Attack requires a multi-layered approach. One of the key steps is to identify and patch any vulnerabilities in your web services. This can be done through regular security testing and code reviews. Additionally, you can implement rate limiting on your web services to restrict the number of requests that can be made from a particular IP address. This can help prevent attackers from using the reflection technique to amplify their attack.
Best Security Practices to Protect Your Network
In addition to the specific measures to prevent Web Service Amplification Attacks, there are some general best practices that can help protect your network. These include implementing strong access controls to restrict access to your network and services, monitoring your network traffic for suspicious activity, and staying up-to-date with the latest security patches and updates for your software and systems.
Conclusion
In conclusion, Web Service Amplification Attacks are a serious threat to your network and services. By understanding how they work and implementing best security practices, you can reduce the risk of a successful attack. Remember to regularly test and update your security measures to stay ahead of evolving threats.